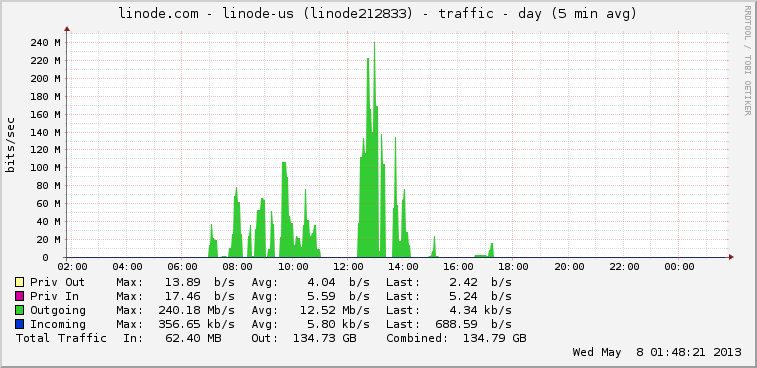
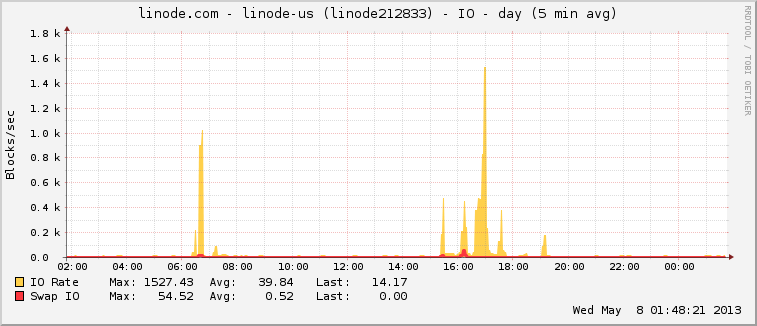
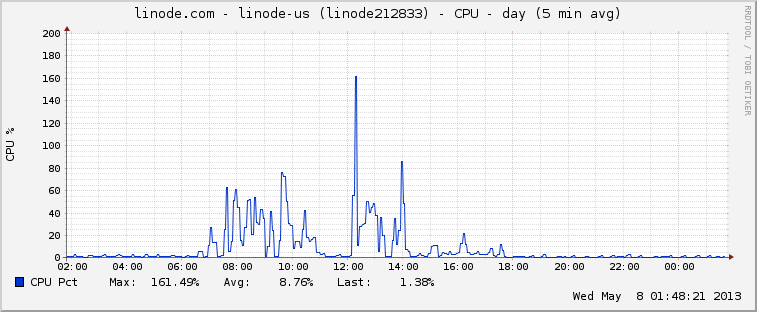
近期服务器,总是收到IO,CPU的报警。
每天某一时刻,IO,CPU, 网络负载值非常高,并不是我的应用流量大。唯一的原因就是服务器被攻击了。
下面4幅图为服务器异常时的状态。
应用软件设置:
- Open-SSH: SSH登陆
- MySQL: 数据库服务器
- Tomcat: Java Web服务器
- Nginx: Http服务器
- php-cgi: PHP脚本解析服务
服务器的端口设置:
~# netstat -nlt
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:1723 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 127.0.0.1:8005 :::* LISTEN
tcp6 0 0 :::8009 :::* LISTEN
tcp6 0 0 :::8080 :::* LISTEN
找到攻击源:
发现在tomcat7/webapps下面,部署了一个我不认识的应用。
找到tomcat7/logs日志,查看是否有使用过Tomcat管理后台
~ tomcat7/logs# ls manager*
manager.2012-07-01.log manager.2013-04-01.log manager.2013-04-25.log
manager.2012-08-21.log manager.2013-04-05.log manager.2013-04-26.log
manager.2012-10-31.log manager.2013-04-08.log manager.2013-04-30.log
manager.2012-11-01.log manager.2013-04-09.log manager.2013-05-01.log
manager.2012-12-26.log manager.2013-04-16.log manager.2013-05-06.log
manager.2013-01-23.log manager.2013-04-17.log manager.2013-05-07.log
manager.2013-03-01.log manager.2013-04-23.log
真被我发现了!!这么多文件操作,我自己并没有这么多的使用。
我们看一下黑客在管理后台干了什么。
~ /tomcat7/logs# vi manager.2013-05-06.log
May 6, 2013 2:20:48 PM org.apache.catalina.core.ApplicationContext log
INFO: HTMLManager: list: Listing contexts for virtual host 'localhost'
May 6, 2013 2:33:45 PM org.apache.catalina.core.ApplicationContext log
INFO: HTMLManager: list: Listing contexts for virtual host 'localhost'
May 6, 2013 2:34:00 PM org.apache.catalina.core.ApplicationContext log
SEVERE: HTMLManager: FAIL - Deploy Upload Failed, Exception: java.io.FileNotFoundException: /root/toolkit/tomcat7/webapps/51.war (Permission denied)
java.io.IOException: java.io.FileNotFoundException: /root/toolkit/tomcat7/webapps/51.war (Permission denied)
at org.apache.catalina.core.ApplicationPart.write(ApplicationPart.java:123)
at org.apache.catalina.manager.HTMLManagerServlet.upload(HTMLManagerServlet.java:332)
at org.apache.catalina.manager.HTMLManagerServlet.doPost(HTMLManagerServlet.java:211)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:641)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:722)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:305)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:210)
at org.apache.catalina.filters.CsrfPreventionFilter.doFilter(CsrfPreventionFilter.java:186)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:243)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:210)
at org.apache.catalina.filters.SetCharacterEncodingFilter.doFilter(SetCharacterEncodingFilter.java:108)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:243)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:210)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:225)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:169)
at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:581)
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:168)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:98)
at org.apache.catalina.valves.AccessLogValve.invoke(AccessLogValve.java:927)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:118)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:407)
at org.apache.coyote.http11.AbstractHttp11Processor.process(AbstractHttp11Processor.java:999)
at org.apache.coyote.AbstractProtocol$AbstractConnectionHandler.process(AbstractProtocol.java:565)
at org.apache.tomcat.util.net.JIoEndpoint$SocketProcessor.run(JIoEndpoint.java:309)
at java.util.concurrent.ThreadPoolExecutor$Worker.runTask(ThreadPoolExecutor.java:886)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:908)
at java.lang.Thread.run(Thread.java:662)
Caused by: java.io.FileNotFoundException: /root/toolkit/tomcat7/webapps/51.war (Permission denied)
at java.io.FileOutputStream.open(Native Method)
at java.io.FileOutputStream.(FileOutputStream.java:194)
at java.io.FileOutputStream.(FileOutputStream.java:145)
at org.apache.tomcat.util.http.fileupload.disk.DiskFileItem.write(DiskFileItem.java:457)
at org.apache.catalina.core.ApplicationPart.write(ApplicationPart.java:121)
... 26 more
May 6, 2013 2:34:00 PM org.apache.catalina.core.ApplicationContext log
INFO: HTMLManager: list: Listing contexts for virtual host 'localhost'
上传名叫 51.war 的包程序在到tomcat/webapps目录。
再来找到黑客是如何获得后台访问权限的
~ vi localhost_access_log.2013-05-06.txt
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - tomcat [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 200 19009
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:20:49 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - - [06/May/2013:14:33:39 +0000] "GET /manager/html HTTP/1.1" 401 2486
218.15.154.174 - tomcat [06/May/2013:14:33:45 +0000] "GET /manager/html HTTP/1.1" 200 17513
218.15.154.174 - tomcat [06/May/2013:14:33:46 +0000] "GET /manager/images/tomcat.gif HTTP/1.1" 200 2066
218.15.154.174 - tomcat [06/May/2013:14:33:46 +0000] "GET /manager/images/asf-logo.gif HTTP/1.1" 200 7279
218.15.154.174 - tomcat [06/May/2013:14:34:00 +0000] "POST /manager/html/upload?org.apache.catalina.filters.CSRF_NONCE=64E6C202103BF3113A72485F80F5133F HTTP/1.1" 200 17638
218.15.154.174 - - [06/May/2013:14:34:11 +0000] "GET /doc HTTP/1.1" 302 -
218.15.154.174 - - [06/May/2013:14:34:11 +0000] "GET /doc/ HTTP/1.1" 200 3309
黑客的扫描程序实验多次后,终于发现了管理后台的密码,并成功登陆
218.15.154.174 – tomcat [06/May/2013:14:20:49 +0000] “GET /manager/html HTTP/1.1” 200 19009
上传自己的程序包
218.15.154.174 – tomcat [06/May/2013:14:34:00 +0000] “POST /manager/html/upload?org.apache.catalina.filters.CSRF_NONCE=64E6C202103BF3113A72485F80F5133F HTTP/1.1” 200 17638
发现黑客的手段后,果断采取防御措施
1. 暂停tomcat的运行
2. 进入webapps目录,删除黑客上传的文件和文件包
3. 分析日志找到攻击者的IP
4. 把这些IP加到iptabls黑名单中
5. 关闭Tomcat管理控制台
分析日志找到攻击者的IP
183.191.4.235
58.180.70.160
113.30.74.125
113.30.106.92
124.160.217.200
218.15.154.174
61.187.94.66
180.179.206.10
187.188.175.49
65.126.238.4
61.167.33.222
54.228.209.57
95.211.121.136
77.79.125.2
218.15.154.174
222.184.121.15
182.140.241.19
121.199.27.236
116.55.226.215
124.129.18.178
109.186.134.160
61.187.94.66
101.226.33.208
101.226.51.226
112.64.235.89
14.63.196.181
113.30.106.90
109.186.134.160
58.180.70.160
49.156.145.2
61.191.31.27
14.17.18.152
113.30.106.95
61.187.94.66
61.187.94.66
101.226.65.106
180.153.163.191
110.4.89.42
61.187.94.66
109.186.134.160
80.241.209.155
85.17.156.16
218.15.154.174
121.199.27.236
61.187.94.66
113.30.74.125
61.191.31.27
121.189.59.207
82.80.248.188
203.174.60.2
182.140.241.19
124.129.18.178
14.63.196.181
49.156.145.2
199.254.238.207
206.172.16.30
61.167.33.222
203.174.60.2
65.126.238.4
59.188.29.254
118.180.7.60
221.12.174.123
46.32.254.6
59.188.29.254
223.16.9.122
把这些IP加到黑名单中
iptables -I INPUT -s 183.191.4.235 -j DROP
iptables -I INPUT -s 58.180.70.160 -j DROP
iptables -I INPUT -s 113.30.74.125 -j DROP
iptables -I INPUT -s 113.30.106.92 -j DROP
iptables -I INPUT -s 124.160.217.200 -j DROP
iptables -I INPUT -s 218.15.154.174 -j DROP
iptables -I INPUT -s 61.187.94.66 -j DROP
iptables -I INPUT -s 180.179.206.10 -j DROP
iptables -I INPUT -s 187.188.175.49 -j DROP
iptables -I INPUT -s 65.126.238.4 -j DROP
iptables -I INPUT -s 61.167.33.222 -j DROP
iptables -I INPUT -s 54.228.209.57 -j DROP
iptables -I INPUT -s 95.211.121.136 -j DROP
iptables -I INPUT -s 77.79.125.2 -j DROP
iptables -I INPUT -s 222.184.121.15 -j DROP
iptables -I INPUT -s 182.140.241.19 -j DROP
iptables -I INPUT -s 121.199.27.236 -j DROP
iptables -I INPUT -s 116.55.226.215 -j DROP
iptables -I INPUT -s 124.129.18.178 -j DROP
iptables -I INPUT -s 109.186.134.160 -j DROP
iptables -I INPUT -s 101.226.33.208 -j DROP
iptables -I INPUT -s 101.226.51.226 -j DROP
iptables -I INPUT -s 112.64.235.89 -j DROP
iptables -I INPUT -s 14.63.196.181 -j DROP
iptables -I INPUT -s 113.30.106.90 -j DROP
iptables -I INPUT -s 49.156.145.2 -j DROP
iptables -I INPUT -s 61.191.31.27 -j DROP
iptables -I INPUT -s 14.17.18.152 -j DROP
iptables -I INPUT -s 113.30.106.95 -j DROP
iptables -I INPUT -s 101.226.65.106 -j DROP
iptables -I INPUT -s 180.153.163.191 -j DROP
iptables -I INPUT -s 110.4.89.42 -j DROP
iptables -I INPUT -s 80.241.209.155 -j DROP
iptables -I INPUT -s 85.17.156.16 -j DROP
iptables -I INPUT -s 121.189.59.207 -j DROP
iptables -I INPUT -s 82.80.248.188 -j DROP
iptables -I INPUT -s 203.174.60.2 -j DROP
iptables -I INPUT -s 14.63.196.181 -j DROP
iptables -I INPUT -s 199.254.238.207 -j DROP
iptables -I INPUT -s 206.172.16.30 -j DROP
iptables -I INPUT -s 59.188.29.254 -j DROP
iptables -I INPUT -s 118.180.7.60 -j DROP
iptables -I INPUT -s 221.12.174.123 -j DROP
iptables -I INPUT -s 46.32.254.6 -j DROP
iptables -I INPUT -s 223.16.9.122 -j DROP
iptables -I INPUT -s 50.23.210.133 -j DROP
iptables -I INPUT -s 208.109.219.192 -j DROP
iptables -I INPUT -s 50.87.248.103 -j DROP
iptables -I INPUT -s 182.50.130.77 -j DROP
iptables -I INPUT -s 50.87.248.181 -j DROP
iptables -I INPUT -s 50.87.90.193 -j DROP
iptables -I INPUT -s 220.177.198.84 -j DROP
iptables -I INPUT -s 50.62.208.135 -j DROP
iptables -I INPUT -s 162.218.210.232 -j DROP
iptables -I INPUT -s 184.168.193.131 -j DROP
iptables -I INPUT -s 50.63.197.206 -j DROP
iptables -I INPUT -s 174.143.240.181 -j DROP
iptables -I INPUT -s 205.144.171.18 -j DROP
iptables -I INPUT -s 205.144.171.18 -j DROP
iptables -I INPUT -s 108.168.219.178 -j DROP
iptables -I INPUT -s 203.198.63.60 -j DROP
iptables -I INPUT -s 119.18.52.114 -j DROP
iptables -I INPUT -s 91.237.52.5 -j DROP
iptables -I INPUT -s 14.102.254.210 -j DROP
iptables -I INPUT -s 108.168.219.178 -j DROP
iptables -I INPUT -s 173.201.196.146 -j DROP
iptables -I INPUT -s 114.215.113.131 -j DROP
iptables -I INPUT -s 184.168.200.185 -j DROP
iptables -I INPUT -s 139.223.200.149 -j DROP
iptables -I INPUT -s 184.168.27.57 -j DROP
iptables -I INPUT -s 122.155.3.113 -j DROP
iptables -I INPUT -s 113.11.250.65 -j DROP
iptables -I INPUT -s 123.30.209.152 -j DROP
iptables -I INPUT -s 184.168.27.57 -j DROP
iptables -I INPUT -s 122.155.3.113 -j DROP
iptables -I INPUT -s 113.11.250.65 -j DROP
iptables -I INPUT -s 123.30.209.152 -j DROP
iptables -I INPUT -s 103.254.12.144 -j DROP
iptables -I INPUT -s 184.168.27.164 -j DROP
iptables -I INPUT -s 107.170.218.152 -j DROP
iptables -I INPUT -s 72.167.232.144 -j DROP
iptables -I INPUT -s 184.168.200.133 -j DROP
iptables -I INPUT -s 175.102.35.39 -j DROP
iptables -I INPUT -s 184.168.193.208 -j DROP
iptables -I INPUT -s 193.0.61.97 -j DROP
iptables -I INPUT -s 184.168.152.201 -j DROP
iptables -I INPUT -s 31.24.128.43 -j DROP
iptables -I INPUT -s 184.168.193.169 -j DROP
iptables -I INPUT -s 185.76.77.160 -j DROP
iptables -I INPUT -s 208.64.62.17 -j DROP
iptables -I INPUT -s 50.62.176.218 -j DROP
iptables -I INPUT -s 50.76.12.242 -j DROP
iptables -I INPUT -s 208.180.34.230 -j DROP
iptables -I INPUT -s 157.7.188.28 -j DROP
iptables -I INPUT -s 184.168.46.193 -j DROP
iptables -I INPUT -s 184.168.27.26 -j DROP
iptables -I INPUT -s 109.2.222.226 -j DROP
iptables -I INPUT -s 50.62.177.130 -j DROP
iptables -I INPUT -s 188.132.236.186 -j DROP
iptables -I INPUT -s 50.97.138.113 -j DROP
iptables -I INPUT -s 72.167.232.225 -j DROP
iptables -I INPUT -s 182.50.132.104 -j DROP
iptables -I INPUT -s 184.168.193.122 -j DROP
iptables -I INPUT -s 184.168.27.144 -j DROP
iptables -I INPUT -s 63.251.175.215 -j DROP
iptables -I INPUT -s 88.208.252.228 -j DROP
iptables -I INPUT -s 101.50.1.11 -j DROP
iptables -I INPUT -s 218.5.79.103 -j DROP
iptables -I INPUT -s 184.168.193.59 -j DROP
iptables -I INPUT -s 97.74.24.214 -j DROP
iptables -I INPUT -s 50.63.196.134 -j DROP
iptables -I INPUT -s 113.10.222.214 -j DROP
iptables -I INPUT -s 184.168.46.92 -j DROP
iptables -I INPUT -s 50.63.197.67 -j DROP
iptables -I INPUT -s 184.168.192.45 -j DROP
iptables -I INPUT -s 182.50.130.111 -j DROP
iptables -I INPUT -s 37.77.3.133 -j DROP
iptables -I INPUT -s 182.50.130.14 -j DROP
iptables -I INPUT -s 184.168.193.121 -j DROP
iptables -I INPUT -s 182.50.130.114 -j DROP
iptables -I INPUT -s 69.16.197.227 -j DROP
iptables -I INPUT -s 97.74.24.172 -j DROP
iptables -I INPUT -s 50.62.208.191 -j DROP
iptables -I INPUT -s 50.62.161.7 -j DROP
iptables -I INPUT -s 82.200.247.241 -j DROP
iptables -I INPUT -s 216.245.192.26 -j DROP
iptables -I INPUT -s 122.155.16.127 -j DROP
iptables -I INPUT -s 50.62.177.161 -j DROP
iptables -I INPUT -s 50.22.62.68 -j DROP
iptables -I INPUT -s 5.101.157.89 -j DROP
iptables -I INPUT -s 70.32.98.71 -j DROP
iptables -I INPUT -s 50.62.176.42 -j DROP
iptables -I INPUT -s 50.62.161.74 -j DROP
iptables -I INPUT -s 106.186.125.120 -j DROP
iptables -I INPUT -s 94.103.47.8 -j DROP
iptables -I INPUT -s 23.101.136.55 -j DROP
iptables -I INPUT -s 185.50.196.214 -j DROP
iptables -I INPUT -s 184.168.200.12 -j DROP
iptables -I INPUT -s 103.233.98.157 -j DROP
iptables -I INPUT -s 50.62.161.38 -j DROP
iptables -I INPUT -s 50.206.14.7 -j DROP
iptables -I INPUT -s 118.186.240.109 -j DROP
iptables -I INPUT -s 182.50.130.114 -j DROP
iptables -I INPUT -s 173.230.136.186 -j DROP
iptables -I INPUT -s 50.63.197.69 -j DROP
iptables -I INPUT -s 194.247.174.66 -j DROP
~ iptables-save > /etc/iptables.up.rules
~ iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP all -- 223.16.9.122 anywhere
DROP all -- 327458.vps-10.com anywhere
DROP all -- 221.12.174.123 anywhere
DROP all -- 118.180.7.60 anywhere
DROP all -- smtp.efaxonline.com anywhere
DROP all -- van-router-01.boats.com anywhere
DROP all -- seattle207.riseup.net anywhere
DROP all -- 14.63.196.181 anywhere
DROP all -- 203.174.60.2 anywhere
DROP all -- bzq-82-80-248-188.static.dcenter.bezeqint.net anywhere
DROP all -- 121.189.59.207 anywhere
DROP all -- hosted-by.leaseweb.com anywhere
DROP all -- ip-155-209-241-80.static.contabo.net anywhere
DROP all -- 110.4.89.42 anywhere
DROP all -- 180.153.163.191 anywhere
DROP all -- 101.226.65.106 anywhere
DROP all -- 113.30.106.95 anywhere
DROP all -- 14.17.18.152 anywhere
DROP all -- 61.191.31.27 anywhere
DROP all -- smtpmail8102.brixmail.com anywhere
DROP all -- 113.30.106.90 anywhere
DROP all -- 14.63.196.181 anywhere
DROP all -- 112.64.235.89 anywhere
DROP all -- 101.226.51.226 anywhere
DROP all -- 101.226.33.208 anywhere
DROP all -- 109-186-134-160.bb.netvision.net.il anywhere
DROP all -- 124.129.18.178 anywhere
DROP all -- 215.226.55.116.broad.km.yn.dynamic.163data.com.cn anywhere
DROP all -- 121.199.27.236 anywhere
DROP all -- 182.140.241.19 anywhere
DROP all -- 222.184.121.15 anywhere
DROP all -- reverse-77-79-125-2.grid.com.tr anywhere
DROP all -- 95.211.121.136 anywhere
DROP all -- ec2-54-228-209-57.eu-west-1.compute.amazonaws.com anywhere
DROP all -- 61.167.33.222 anywhere
DROP all -- wickedgoodcharcoal.com anywhere
DROP all -- fixed-188-175-49.iusacell.net anywhere
DROP all -- 180.179.206.10 anywhere
DROP all -- 61.187.94.66 anywhere
DROP all -- 218.15.154.174 anywhere
DROP all -- 124.160.217.200 anywhere
DROP all -- 113.30.106.92 anywhere
DROP all -- 113.30.74.125 anywhere
DROP all -- 58.180.70.160 anywhere
DROP all -- 235.4.191.183.adsl-pool.sx.cn anywhere
DROP all -- 124.115.0.199 anywhere
DROP all -- cust.static.62-202-18-26.swisscomdata.ch anywhere
DROP all -- 60-199-223-196.static.tfn.net.tw anywhere
DROP all -- 148.208.222.7 anywhere
DROP all -- woman22.ru anywhere
关闭Tomcat管理控制台
把tomcat-users.xml文件的内容都注释掉。
vi ~/tomcat7/conf/tomcat-users.xml
<tomcat-users>
<!–
<role rolename=”manager-gui”/>
<user username=”tomcat” password=”bsspirit” roles=”manager-gui”/>
<user username=”both” password=”tomcat” roles=”tomcat,role1″/>
<user username=”role1″ password=”tomcat” roles=”role1″/>
–>
</tomcat-users>
重启Tomcat服务器!完成Tomcat防御。
服务器的root账号,并没有被破解。为了安全还是换一个吧,攻击手段并不高明,只是我们疏于防范了。
再次给使用TOMCAT的用户提个醒,平时不要打开管理控制台,会被黑客当枪用的。