操作系统实用工具系列文章,将介绍基于Linux ubuntu的各种工具软件的配置和使用。有些工具大家早已耳熟能详,有些工具经常用到但确依然陌生。我将记录我在使用操作系统时,安装及配置工具上面的一些方法,把使用心得记录下来也便于自己的以后查找和回忆。
关于作者:
- 张丹(Conan), 程序员R,Nodejs,Java
- weibo:@Conan_Z
- blog: http://blog.fens.me
- email: bsspirit@gmail.com
转载请注明出处:
http://blog.fens.me/ubuntu-vpn-ipsec
前言
随着iphone的IOS版本升级到了10以后,PPTP协议的VPN不再支持了。为了能够继续使用Google的服务,提升对信息的准确查询,那么只能基于新的标准,再重新搭建一套的环境。用PPTP搭建VPN请参考文章:在Ubuntu上安装PPTP VPN服务
本文只是在纯技术层面进行介绍,如何使用IPSEC协议来搭建VPN服务。
目录
- IPSEC协议
- 服务器端程序搭建
- 客户端测试
- 剖析脚本
1. IPSEC协议
IPSec(Internet Protocol Security)是一种开放标准的框架结构,通过使用加密的安全服务以确保在 Internet 协议 (IP) 网络上进行保密而安全的通讯。它通过端对端的安全性来提供主动的保护以防止专用网络与 Internet 的攻击。在通信中,只有发送方和接收方才是唯一必须了解 IPSec 保护的计算机。
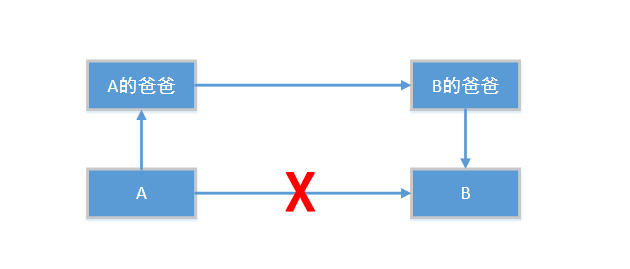
IPSEC包封装过程
我们有一个生活中简单的例子,来说明一下IPSEC包封装过程。
假设2个小朋友A和B要邮寄包裹,A要寄东西给B,A的爸爸和B的爸爸正巧在一家公司工作,所以A就把给B的包裹,交给了A的爸爸,再由A的爸爸转交给B的爸爸,B的爸爸最后把包裹给B的手中。回寄也一样,通过B的父亲发回给A的父亲再回给A。
这种通讯实现方式要依赖以下几个因素:
- A的爸爸和B的爸爸可以见到。
- A发包裹,把包裹交给A的爸爸。
- A的爸爸收到儿子的包裹后,能够正确的处理,并且重新包装过的包裹能够正确送出去。
- 另外一端,B的爸爸收到包裹开以后,能够正确地交给B。
- 反过来的流程一样。
2. 服务器端程序搭建
本来安装和配置IPSEC服务,不是一件容易,但无意中发现了 IPsec VPN 服务器一键安装脚本 项目,让这一切都变得非常简单。感谢项目作者 Lin Song!
我的服务器环境是Ubuntu 16.04 LTS,主机在香港。
一键安装,只需要3个步骤。
- 从网上下载一个shell脚步。
- 修改登录的用户名、密码、秘钥。
- 运行脚本
1. 从网上下载一个shell脚步。
~ wget https://git.io/vpnsetup -O vpnsetup.sh
2. 修改登录的用户名、密码、秘钥。
~ vi vpnsetup.sh
# Define your own values for these variables
# - IPsec pre-shared key, VPN username and password
# - All values MUST be placed inside 'single quotes'
# - DO NOT use these characters within values: \ " '
YOUR_IPSEC_PSK='abc' # 设置密钥
YOUR_USERNAME='conan' # 设置用户名
YOUR_PASSWORD='12345678' # 设置密码
# 省略...
3. 运行脚本
~ sudo sh vpnsetup.sh
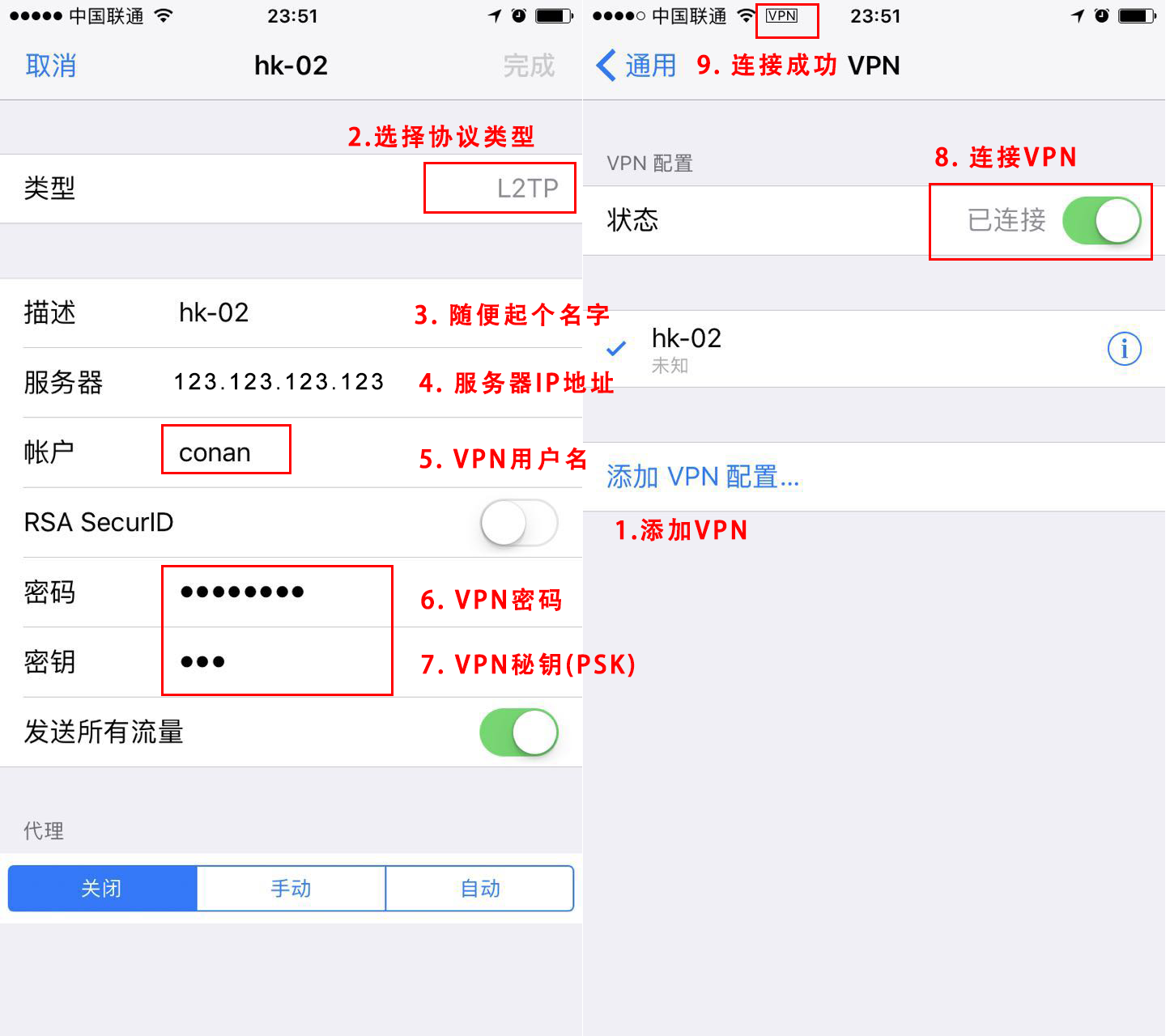
3. 客户端测试
我的iphone-7手机,OS的版本为10.3.3,打开VPN的设置界面。设置–>通用–>VPN–>添加VPN配置。
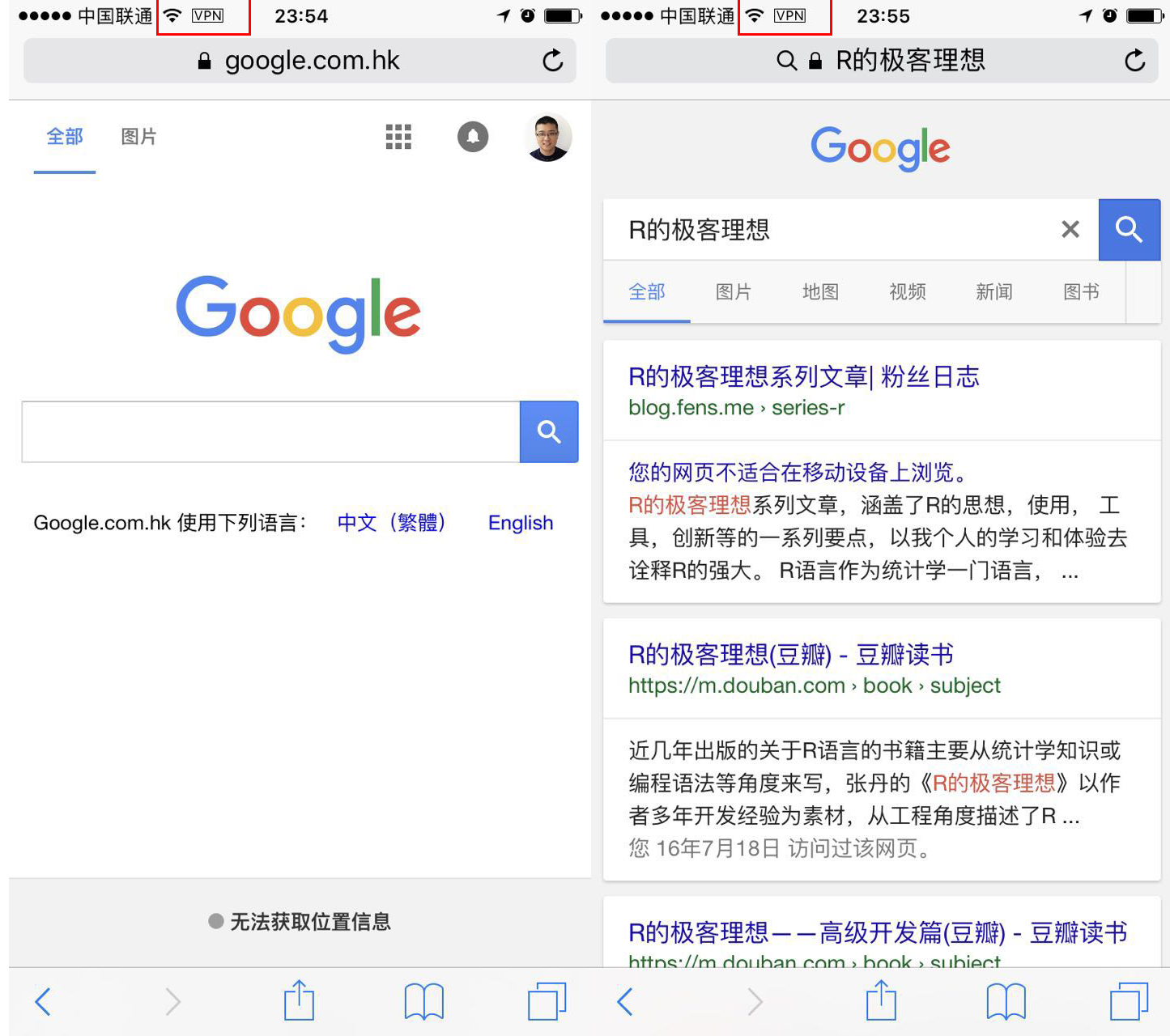
测试VPN是否正常工作,打开浏览器,访问www.google.com网页。
如果你也看到google,那么恭喜你就配置成功了!!
4. 剖析脚本
通过上面的操作,我们已经完成了VPN服务器的搭建,那么为什么还要有剖析脚本这个部分呢。我本来也自己尝试着参考网上的一些文章,以及一些开源VPN服务器的说明去配置,但花了几天的时间,一直都没有完全调通。这里其实有不少的网络知识点,是需要我们理解和掌握的。
正好可以查看 vpnsetup.sh 文件,一步一步的分析。
4.1 安装依赖包。
// 更新源
~ apt-get update
// 基础工具包
~ apt-get -yq install wget dnsutils openssl
~ apt-get -yq install iproute gawk grep sed net-tools
// VPN相关的包
~ apt-get -yq install libnss3-dev libnspr4-dev pkg-config libpam0g-dev \
libcap-ng-dev libcap-ng-utils libselinux1-dev \
libcurl4-nss-dev flex bison gcc make \
libunbound-dev libnss3-tools libevent-dev
~ apt-get -yq --no-install-recommends install xmlto
~ apt-get -yq install ppp xl2tpd
// SSH相关的包
~ apt-get -yq install fail2ban
~ apt-get -yq install libsystemd-dev
4.2 下载及安装libreswan包
~ wget https://download.libreswan.org/libreswan-3.21.tar.gz
~ tar xzf libreswan-3.21.tar.gz && cd libreswan-3.21
~ make -s programs && make -s install
4.3 修改配置文件
- /etc/ipsec.conf
- /etc/ipsec.secrets
- /etc/xl2tpd/xl2tpd.conf
- /etc/ppp/options.xl2tpd
- /etc/ppp/chap-secrets
- /etc/ipsec.d/passwd
- /etc/sysctl.conf
- /etc/iptables.rules
4.3.1 查看/etc/ipsec.conf
~ vi /etc/ipsec.conf
version 2.0
config setup
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:!192.168.42.0/24,%v4:!192.168.43.0/24
protostack=netkey
nhelpers=0
interfaces=%defaultroute
uniqueids=no
conn shared
left=%defaultroute
leftid=123.123.123.123 # 当前服务器的IP
right=%any
encapsulation=yes
authby=secret
pfs=no
rekey=no
keyingtries=5
dpddelay=30
dpdtimeout=120
dpdaction=clear
ike=3des-sha1,3des-sha2,aes-sha1,aes-sha1;modp1024,aes-sha2,aes-sha2;modp1024,aes256-sha2_512
phase2alg=3des-sha1,3des-sha2,aes-sha1,aes-sha2,aes256-sha2_512
sha2-truncbug=yes
conn l2tp-psk
auto=add
leftprotoport=17/1701
rightprotoport=17/%any
type=transport
phase2=esp
also=shared
conn xauth-psk
auto=add
leftsubnet=0.0.0.0/0
rightaddresspool=192.168.43.10-192.168.43.250
modecfgdns1=8.8.8.8 # DNS 解析1
modecfgdns2=8.8.4.4 # DNS 解析2
leftxauthserver=yes
rightxauthclient=yes
leftmodecfgserver=yes
rightmodecfgclient=yes
modecfgpull=yes
xauthby=file
ike-frag=yes
ikev2=never
cisco-unity=yes
also=shared
4.3.2 查看/etc/ipsec.secrets
~ vi /etc/ipsec.secrets
%any %any : PSK "abc" # 设置ipsec的登录权限,秘钥为abc
4.3.3 查看/etc/xl2tpd/xl2tpd.conf
~ vi /etc/xl2tpd/xl2tpd.conf
[global]
port = 1701 # 连接端口
[lns default]
ip range = 192.168.42.10-192.168.42.250 # VPN内网IP段
local ip = 192.168.42.1 # 主机的内网IP
require chap = yes # 要求chap身份认证模式
refuse pap = yes # 拒绝pap身份认证模式
require authentication = yes # 要求认证登录
name = l2tpd # 服务名称为l2tpd
pppoptfile = /etc/ppp/options.xl2tpd # ppp的配置文件
length bit = yes
4.3.4 查看/etc/ppp/options.xl2tpd
~ vi /etc/ppp/options.xl2tpd
ipcp-accept-local
ipcp-accept-remote
ms-dns 8.8.8.8 # DNS 解析1
ms-dns 8.8.4.4 # DNS 解析2
noccp
auth
mtu 1280
mru 1280
proxyarp # arp代理
lcp-echo-failure 4
lcp-echo-interval 30
connect-delay 5000
4.3.5 查看 /etc/ppp/chap-secrets
~ vi /etc/ppp/chap-secrets
# Secrets for authentication using CHAP
# client server secret IP addresses
# 用户名 服务类型 密码 分配的ip地址
"conan" l2tpd "12345678" * # 设置客户端登录账户和密码,4个字段用空格分隔, *表示任意类型
4.3.6 查看 /etc/ipsec.d/passwd
~ vi /etc/ipsec.d/passwd
conan:$1$rkrg5ssz$3lTGfeeazreqrR79pAoggh1:xauth-psk # 使用秘钥加密后的密码
4.3.7 查看 /etc/sysctl.conf
~ vi /etc/sysctl.conf
kernel.msgmnb = 65536
kernel.msgmax = 65536
kernel.shmmax = 68719476736
kernel.shmall = 4294967296
net.ipv4.ip_forward = 1
net.ipv4.tcp_syncookies = 1
net.ipv4.conf.all.accept_source_route = 0
net.ipv4.conf.default.accept_source_route = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.lo.send_redirects = 0
net.ipv4.conf.eth0.send_redirects = 0
net.ipv4.conf.all.rp_filter = 0
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.lo.rp_filter = 0
net.ipv4.conf.eth0.rp_filter = 0
net.ipv4.icmp_echo_ignore_broadcasts = 1
net.ipv4.icmp_ignore_bogus_error_responses = 1
net.core.wmem_max = 12582912
net.core.rmem_max = 12582912
net.ipv4.tcp_rmem = 10240 87380 12582912
net.ipv4.tcp_wmem = 10240 87380 12582912
4.3.8 查看/etc/iptables.rules
~ vi /etc/iptables.rules
# Modified by hwdsl2 VPN script
# Generated by iptables-save v1.6.0 on Mon Sep 18 22:36:46 2017
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
-A POSTROUTING -s 192.168.42.0/24 -o eth0 -j MASQUERADE
-A POSTROUTING -s 192.168.43.0/24 -o eth0 -m policy --dir out --pol none -j MASQUERADE
COMMIT
# Completed on Mon Sep 18 22:36:46 2017
# Generated by iptables-save v1.6.0 on Mon Sep 18 22:36:46 2017
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -p udp -m udp --dport 1701 -m policy --dir in --pol none -j DROP
-A INPUT -m conntrack --ctstate INVALID -j DROP
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p udp -m multiport --dports 500,4500 -j ACCEPT
-A INPUT -p udp -m udp --dport 1701 -m policy --dir in --pol ipsec -j ACCEPT
-A INPUT -p udp -m udp --dport 1701 -j DROP
-A FORWARD -m conntrack --ctstate INVALID -j DROP
-A FORWARD -i eth0 -o ppp+ -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -i ppp+ -o eth0 -j ACCEPT
-A FORWARD -s 192.168.42.0/24 -d 192.168.42.0/24 -i ppp+ -o ppp+ -j ACCEPT
-A FORWARD -d 192.168.43.0/24 -i eth0 -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
-A FORWARD -s 192.168.43.0/24 -o eth0 -j ACCEPT
-A FORWARD -s 10.1.20.0/24 -j ACCEPT
-A FORWARD -j DROP
COMMIT
# Completed on Mon Sep 18 22:36:46 2017
4.4 查看连接日志
接下来,我们用手机连接VPN,然后查看日志输出 。
连接日志
~ tail -f /var/log/syslog
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: Connection established to 36.102.226.172, 65287. Local: 21666, Remote: 20 (ref=0/0). LNS session is 'default'
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: start_pppd: I'm running:
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "/usr/sbin/pppd"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "passive"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "nodetach"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "192.168.42.1:192.168.42.10"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "refuse-pap"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "auth"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "require-chap"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "name"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "l2tpd"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "file"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "/etc/ppp/options.xl2tpd"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "plugin"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "pppol2tp.so"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "pppol2tp"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "8"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "pppol2tp_lns_mode"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "pppol2tp_tunnel_id"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "21666"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "pppol2tp_session_id"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: "21136"
Sep 19 13:54:28 i-vtnhoxsp xl2tpd[20115]: Call established with 36.102.226.172, Local: 21136, Remote: 10537, Serial: 1
Sep 19 13:54:28 i-vtnhoxsp pppd[23553]: Plugin pppol2tp.so loaded.
Sep 19 13:54:28 i-vtnhoxsp pppd[23553]: pppd 2.4.7 started by root, uid 0
Sep 19 13:54:28 i-vtnhoxsp pppd[23553]: Using interface ppp0
Sep 19 13:54:28 i-vtnhoxsp pppd[23553]: Connect: ppp0 <-->
Sep 19 13:54:28 i-vtnhoxsp pppd[23553]: Overriding mtu 1500 to 1280
Sep 19 13:54:28 i-vtnhoxsp pppd[23553]: Overriding mru 1500 to mtu value 1280
Sep 19 13:54:28 i-vtnhoxsp pppd[23553]: Overriding mtu 1500 to 1280
Sep 19 13:54:32 i-vtnhoxsp charon: 05[KNL] 192.168.42.1 appeared on ppp0
Sep 19 13:54:32 i-vtnhoxsp charon: 03[KNL] 192.168.42.1 disappeared from ppp0
Sep 19 13:54:32 i-vtnhoxsp charon: 07[KNL] 192.168.42.1 appeared on ppp0
Sep 19 13:54:32 i-vtnhoxsp pppd[23553]: Cannot determine ethernet address for proxy ARP
Sep 19 13:54:32 i-vtnhoxsp pppd[23553]: local IP address 192.168.42.1
Sep 19 13:54:32 i-vtnhoxsp pppd[23553]: remote IP address 192.168.42.10
Sep 19 13:54:32 i-vtnhoxsp charon: 10[KNL] interface ppp0 activated
断开手机的VPN连接,查看日志。
~ tail -f /var/log/syslog
Sep 19 13:55:53 i-vtnhoxsp xl2tpd[20115]: result_code_avp: result code endianness fix for buggy Apple client. network=768, le=3
Sep 19 13:55:53 i-vtnhoxsp xl2tpd[20115]: control_finish: Connection closed to 36.102.226.172, serial 1 ()
Sep 19 13:55:53 i-vtnhoxsp pppd[23553]: LCP terminated by peer (User request)
Sep 19 13:55:53 i-vtnhoxsp xl2tpd[20115]: Terminating pppd: sending TERM signal to pid 23553
Sep 19 13:55:53 i-vtnhoxsp pppd[23553]: Connect time 1.4 minutes.
Sep 19 13:55:53 i-vtnhoxsp pppd[23553]: Sent 93199 bytes, received 34500 bytes.
Sep 19 13:55:53 i-vtnhoxsp charon: 06[KNL] interface ppp0 deactivated
Sep 19 13:55:53 i-vtnhoxsp xl2tpd[20115]: result_code_avp: result code endianness fix for buggy Apple client. network=256, le=1
Sep 19 13:55:53 i-vtnhoxsp xl2tpd[20115]: control_finish: Connection closed to 36.102.226.172, port 65287 (), Local: 21666, Remote: 20
Sep 19 13:55:53 i-vtnhoxsp charon: 03[KNL] 192.168.42.1 disappeared from ppp0
Sep 19 13:55:53 i-vtnhoxsp pppd[23553]: Overriding mtu 1500 to 1280
Sep 19 13:55:53 i-vtnhoxsp pppd[23553]: Overriding mru 1500 to mtu value 1280
Sep 19 13:55:53 i-vtnhoxsp pppd[23553]: Terminating on signal 15
Sep 19 13:55:56 i-vtnhoxsp pppd[23553]: Connection terminated.
Sep 19 13:55:56 i-vtnhoxsp charon: 11[KNL] interface ppp0 deleted
Sep 19 13:55:56 i-vtnhoxsp pppd[23553]: Modem hangup
Sep 19 13:55:56 i-vtnhoxsp pppd[23553]: Exit.
对于脚本的分析,虽然没有给出结论,而且很多配置我还是不太理解。不过要坚持学习,不断的提升自己的能力,不然永远都要等着大牛们提供一键安装的脚本。
转载请注明出处:
http://blog.fens.me/ubuntu-vpn-ipsec


[…] 程序员都知道,不多说了。VPN服务器搭建,请参考文章在Ubuntu上安装IPSEC VPN服务,在Ubuntu上安装PPTP VPN服务 […]